tcpdump

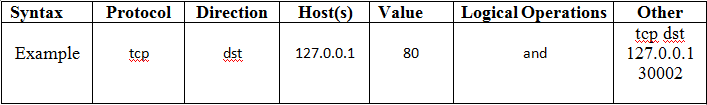
- Protocol
Values: ether, fddi, ip, arp, rarp, decnet, lat, sca, moprc, mopdl, tcp and udp.
If no protocol is specified, all the protocols are used. - Direction
Values: src, dst, src and dst, src or dst
If no source or destination is specified, the "src or dst" keywords are applied. - Host(s)
Values: net, port, host, portrange.
If no host(s) is specified, the "host" keyword is used. - Logical Operations
Values: not, and, or.
Negation ("not") has highest precedence. Alternation ("or") and concatenation ("and") have equal precedence and associate left to right.
- -c : Only capture x number of packets, e.g. 'tcpdump -c 5'
- -e : Get the ethernet header as well.
- -E : Decrypt IPSEC traffic by providing an encryption key.
- -i any : Listen on all interfaces.
- -n : Don't resolve hostnames.
- -nn : Don't resolve hostnames or port names.
- -q : Show less protocol information.
- -s : Set the snaplength, i.e. the amount of data that is being captured in bytes
(use -s0 unless you are intentionally capturing less.) - -S : Print absolute sequence numbers.
- -v, -vv, -vvv : Increase the amount of packet information you get back.
- -X : Show the packet's contents in both hex and ASCII.
- -XX : Same as -X, but also shows the ethernet header.
$ sudo tcpdump tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 96 bytes 10:22:34.335887 IP 209.102.204.138.51056 > 203.147.106.1.51056: UDP, length 45
-v causes tcpdump to print more information about each packet. With -vv tcpdump prints even more information and -vvv produces even more information.
$ sudo tcpdump -v tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 96 bytes 10:37:47.390168 IP (tos 0x0, ttl 114, id 13003, offset 0, flags [none], proto: UDP (17), length: 73) 209.102.204.138.51056 > 203.147.106.1.51056: UDP, length 45
Expressions allow us to trim out various types of traffic and find exactly what we're looking for. There are three main types of expression: type, dir, and proto.
Type options are host, net, and port. Direction is indicated by dir, and there we can have src, dst, src or dst, and src and dst.
-
host
look for traffic based on IP address (also works with hostname if we're not using -n)$ sudo tcpdump host 203.147.106.1
-
src, dst
find traffic from only a source or destination (eliminates one side of a host conversation)$ sudo tcpdump src 203.147.106.1 $ sudo tcpdump dst 209.102.204.138
-
net
capture an entire network using CIDR notation$ sudo tcpdump net 209.102.204.138/24
-
proto
works for tcp, udp, and icmp. Note that we don't have to type proto$ sudo tcpdump icmp
-
port
see only traffic to or from a certain port$ sudo tcpdump port 51506
-
src, dst port
filter based on the source or destination port$ sudo tcpdump src port 51506 $ sudo tcpdump dst port 51508
-
src/dst, port, protocol
combine all three$ sudo tcpdump src port 51506 and tcp $ sudo tcpdump udp and src port 51508
-
We also have the option to filter by a range of ports instead of declaring them individually, and to only see packets that are above or below a certain size.
-
Port Ranges
see traffic to any port in a rangetcpdump portrange 51506-51508
-
Packet Size Filter
only see packets below or above a certain size (in bytes)tcpdump less 64 tcpdump greater 256
We can use the symbols for less than, greater than, and less than or equal / greater than or equal signs as well. -
filtering for size using symbols
tcpdump > 64 tcpdump <= 256
We can write what we're capturing to a file for later use using the -w option, and then to read it back using the -r option. This is an excellent way to capture raw traffic and then run it through various tools later.
The traffic captured in this way is stored in tcpdump format, which is pretty much universal in the network analysis space.
-
Capture all Port 80 Traffic to a File
$ sudo tcpdump -s 1514 port 80 -w capture_file
-
We can also read the packets from a saved file using tcpdump -r
$ sudo tcpdump -r capture_file
We can receive the packets based on the protocol type by specifying one of these protocols - fddi, tr, wlan, ip, ip6, arp, rarp, decnet, tcp and udp. The following example captures only udp packets for the eth0 interface.
$ sudo tcpdump -i eth0 udp
With some of the options described above, here is a capture of exactly two (-c2) ICMP packets.
$ sudo tcpdump -nnvXSs 0 -c2 icmp
tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes
10:55:55.409753 IP (tos 0xc0, ttl 64, id 51895, offset 0, flags [none], proto: ICMP (1), length: 108) 203.147.106.1 > 209.102.204.138: ICMP 203.147.106.1 udp port 51056 unreachable, length 88
IP (tos 0x0, ttl 114, id 54851, offset 0, flags [none], proto: UDP (17), length: 80) 209.102.204.138.51051 > 203.147.106.1.51056: UDP, length 52
0x0000: 45c0 006c cab7 0000 4001 a96a d32b 9492 E..l....@..j.+..
0x0010: d166 cc8a 0303 02fa 0000 0000 4500 0050 .f..........E..P
0x0020: d643 0000 7211 6caa d166 cc8a d32b 9492 .C..r.l..f...+..
0x0030: c76b c76b 003c 3631 80c8 0006 0000 66d6 .k.k.<61......f.
0x0040: d2f8 f329 7698 3516 2def 1329 0001 96fd ...)v.5.-..)....
0x0050: 0031 48a3 81ca 0005 0000 66d6 010c 494e .1H.......f...IN
0x0060: 4c45 5441 5544 494f 4842 0000 LETAUDIOHB..
10:55:56.696589 IP (tos 0xc0, ttl 64, id 51896, offset 0, flags [none], proto: ICMP (1), length: 108) 203.147.106.1 > 209.102.204.138: ICMP 203.147.106.1 udp port 51057 unreachable, length 88
IP (tos 0x0, ttl 114, id 55601, offset 0, flags [none], proto: UDP (17), length: 80) 209.102.204.138.51057 > 203.147.106.1.51057: UDP, length 52
0x0000: 45c0 006c cab8 0000 4001 a969 d32b 9492 E..l....@..i.+..
0x0010: d166 cc8a 0303 02fa 0000 0000 4500 0050 .f..........E..P
0x0020: d931 0000 7211 69bc d166 cc8a d32b 9492 .1..r.i..f...+..
0x0030: c771 c771 003c 3131 80c8 0006 8000 5e94 .q.q.<11......^.
0x0040: d2f8 f32a cf94 face 2dca ccfb 0009 30de ...*....-.....0.
0x0050: 011c eae2 81ca 0005 8000 5e94 010c 494e ..........^...IN
0x0060: 4c45 5441 5544 494f 4842 0000 LETAUDIOHB..
2 packets captured
8 packets received by filter
0 packets dropped by kernel
Ph.D. / Golden Gate Ave, San Francisco / Seoul National Univ / Carnegie Mellon / UC Berkeley / DevOps / Deep Learning / Visualization