AWS CodeDeploy - Deploy an Application from GitHub
In this tutorial, we'll use AWS CodeDeploy to deploy a sample application revision from GitHub to a Red Hat Enterprise Linux (RHEL) instance.
AWS CodeDeploy automates code deployments to Amazon EC2 instances. It deploys applications from Amazon S3 buckets and GitHub repositories.
The following diagram illustrates the flow of a typical AWS CodeDeploy deployment:
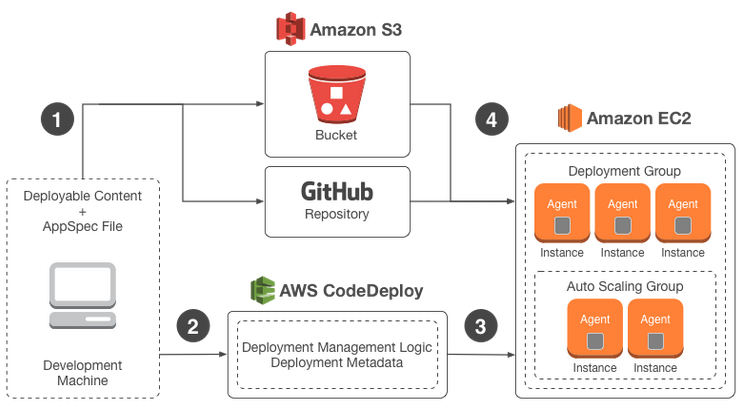
Here are the characteristics of CodeDeploy:
- Deploys our code to a "fleet" of EC2 instances.
- 1-10,000s of insances.
- Automatically schedules updates (multiple AZs).
- Application and Deployment groups described in YAML-formatted files.
- Can reference Auto Scaling Group.
- AWS Management Console, CLI, or APIs.
- Can be used with Check recipes or Puppet scripts.
Get a sample app (SampleApp_Linux.zip) from this link:
Push zip file to Github (CodeDeployGitHubDemo):
$ git add SampleApp_Linux.zip $ git commit -m "initial commit" $ git push
In the navigation pane, choose "Roles", and then choose "Create New Role". Then, in the Role Name box, give the service role a name ("CodeDeployServiceRole:), and then choose Next Step.
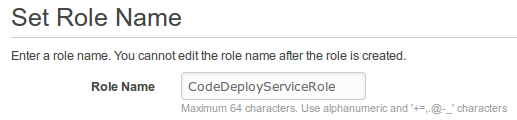
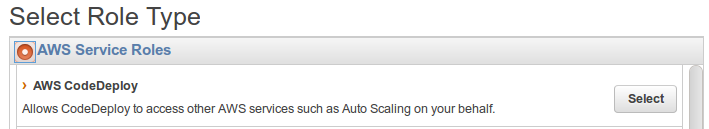
On the Select Role Type page, with AWS Service Roles selected, next to AWS CodeDeploy, choose Select:
On the Attach Policy page, select the box next to the AWSCodeDeployRole policy, and then choose Next Step.
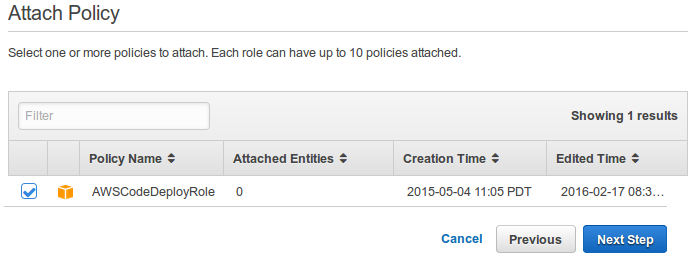
Our Amazon EC2 instances need permission to access the Amazon S3 buckets or GitHub repositories where the applications that will be deployed by AWS CodeDeploy are stored.
To launch Amazon EC2 instances that are compatible with AWS CodeDeploy, we must create an additional IAM role, an instance profile. This role gives AWS CodeDeploy permission to access the Amazon S3 buckets or GitHub repositories where our applications are stored.
In the IAM console, in the navigation pane, choose Policies, and then choose Create Policy.
Next to Create Your Own Policy, choose Select:

In the Policy Name box, type CodeDeployDemo-EC2-Permissions. In the Policy Document box, paste the following:
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"s3:Get*",
"s3:List*"
],
"Effect": "Allow",
"Resource": "*"
}
]
}
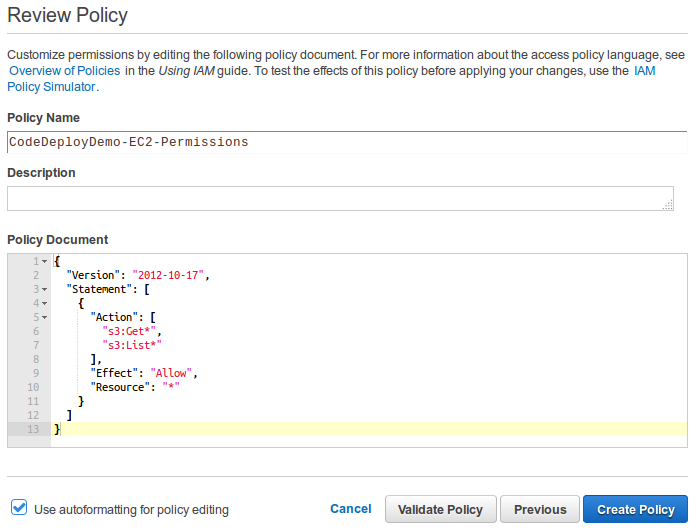
Choose Create Policy.
In the navigation pane, choose Roles, and then choose Create New Role.
In the Role Name box, give the IAM instance profile a name like CodeDeployDemo-EC2, and then choose Next Step.
On the Select Role Type page, next to Amazon EC2, choose Select.
On the Attach Policy page, select the box next to CodeDeployDemo-EC2-Permissions:
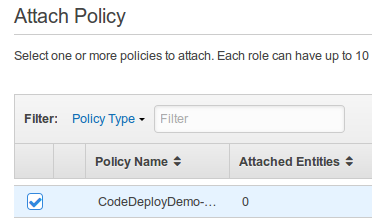
Then, choose Next Step.
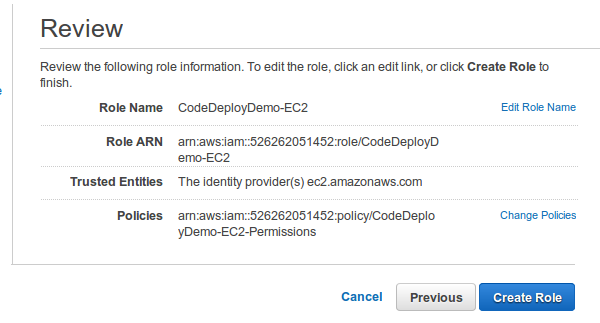
Choose Create Role.
We've now created an IAM instance profile to attach to Amazon EC2 instances.
Now that we've created an IAM instance profile named CodeDeployDemo-EC2-Instance-Profile, let's launch an instance with an appropriate IAM role:
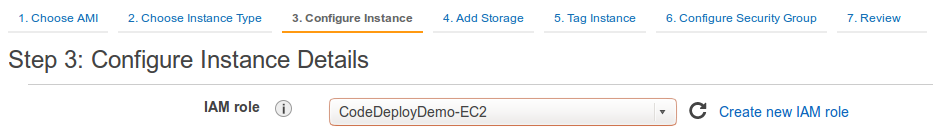
Next to User data, with the As text option selected, type the following to install the AWS CodeDeploy agent as the Amazon EC2 instance is launched:
#!/bin/bash sudo yum -y update sudo yum install -y ruby curl -O https://bootstrap.pypa.io/get-pip.py sudo python get-pip.py sudo pip install awscli cd /home/ec2-user sudo aws s3 cp s3://aws-codedeploy-us-west-1/latest/install . --region us-west-1 sudo chmod +x ./install sudo ./install auto
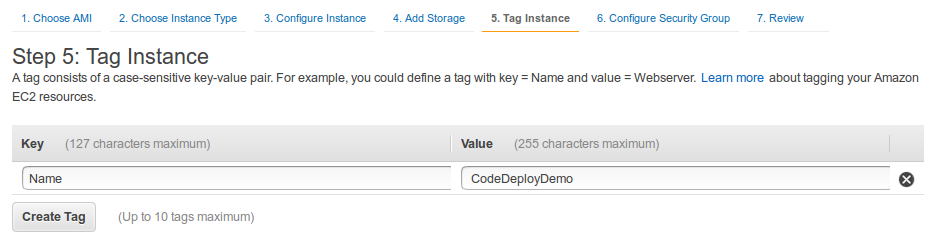
The rest of the steps remain the same as usual.

To see if the AWS CodeDeploy agent is installed and running, sign in to the instance, and run the following command:
$ ssh -i bogo.pem ec2-user@54.153.66.39 [ec2-user@ip-172-31-6-89 ~]$ [ec2-user@ip-172-31-6-89 ~]$ sudo service codedeploy-agent status The AWS CodeDeploy agent is running as PID 26896
The AWS CodeDeploy agent is installed and running as we can see from the output message.
Now we have an instance configured for use in AWS CodeDeploy deployments, and we successfully launched the instance and verified the AWS CodeDeploy agent is running.
In this section, we will use the AWS CodeDeploy console or the AWS CLI to deploy the sample revision from our GitHub repository to the instance.
Our sample revision is a single web page deployed to the instance.
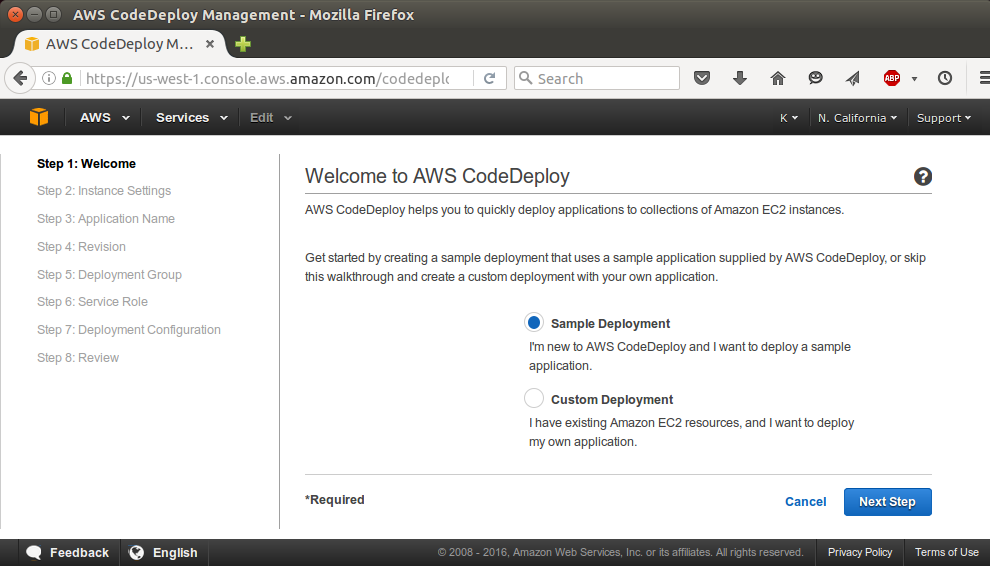
Sign in to the AWS Management Console and open the AWS CodeDeploy console at https://console.aws.amazon.com/codedeploy
.
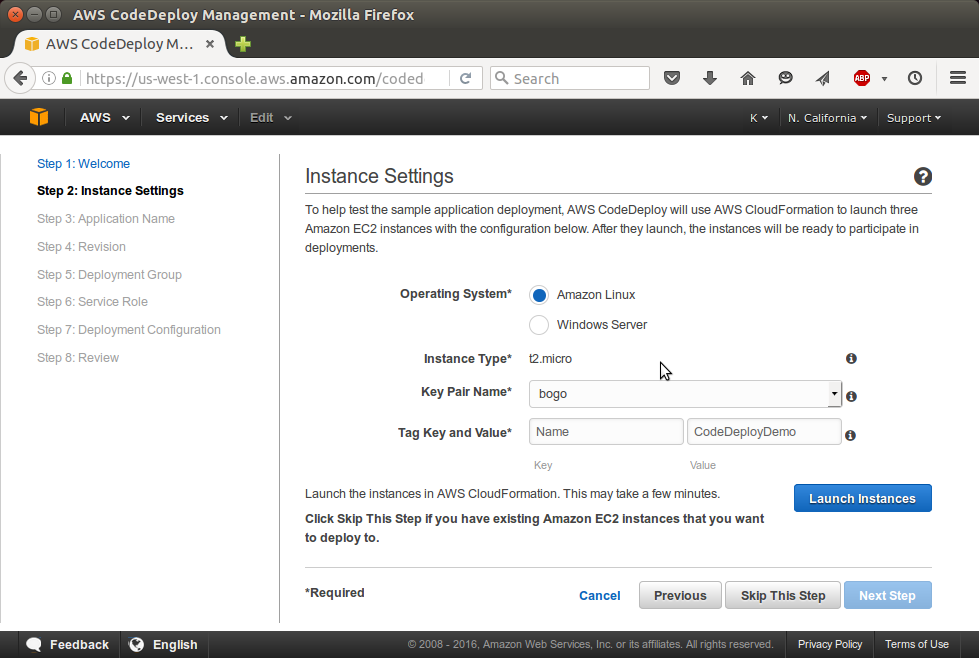
We already have an instance, so click "Skip"
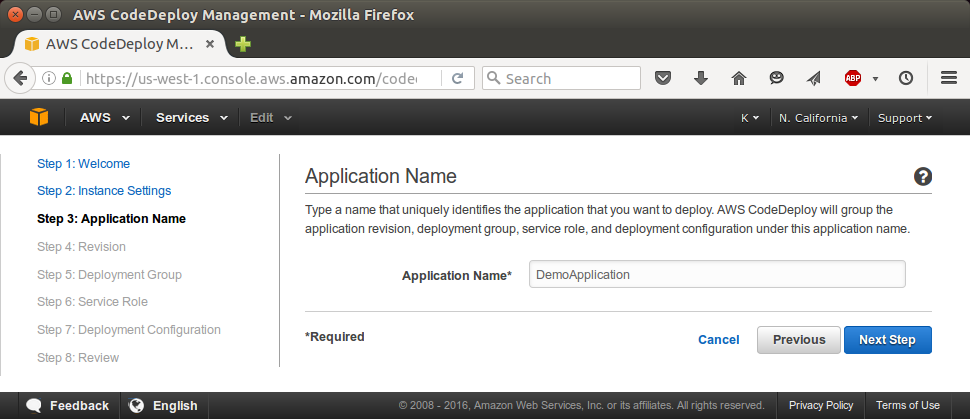
In the Application Name box, type "CodeDeployGitHubDemo-App":
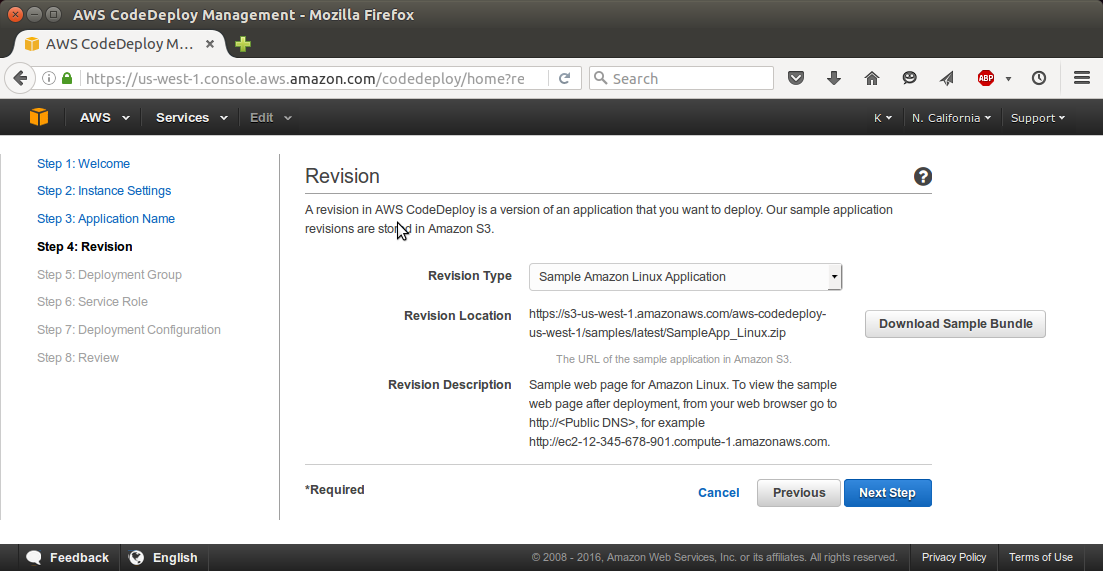
In the Deployment Group Name box, type CodeDeployGitHubDemo-DepGrp:
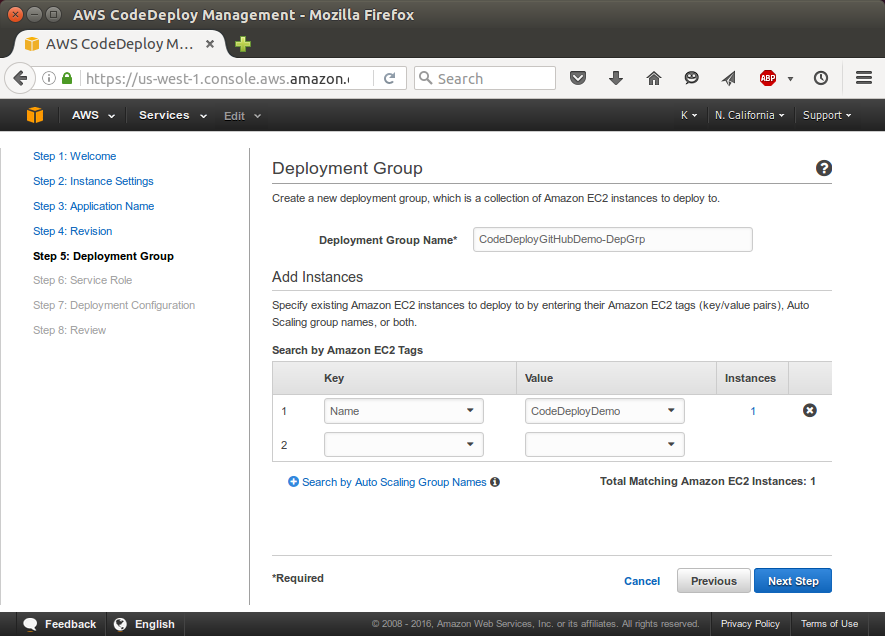
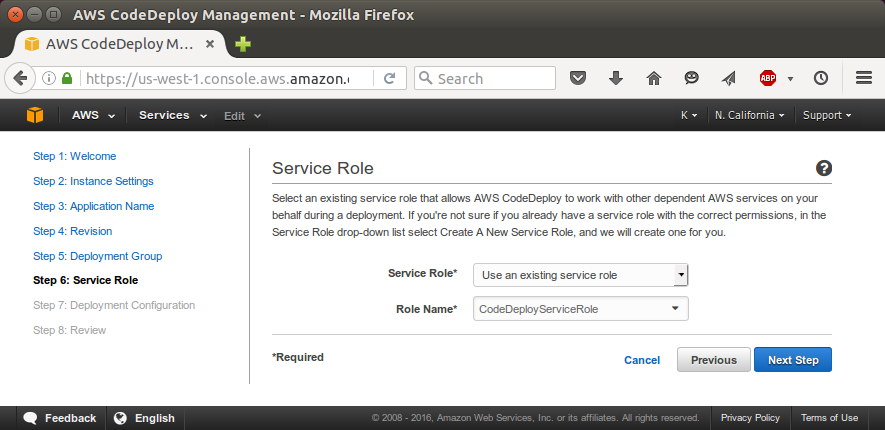
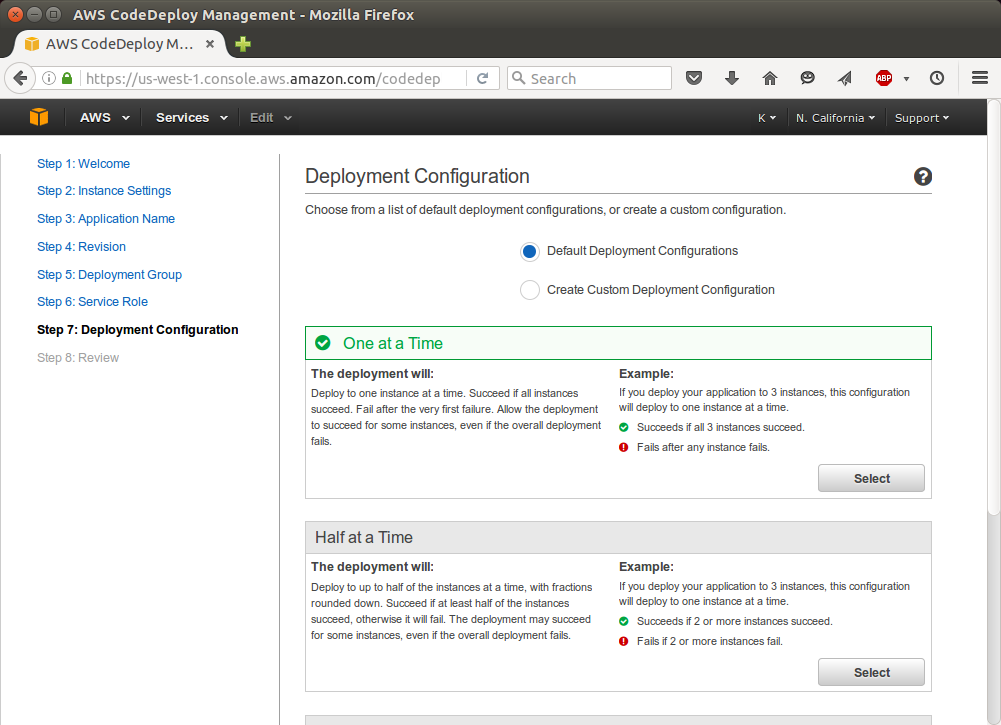
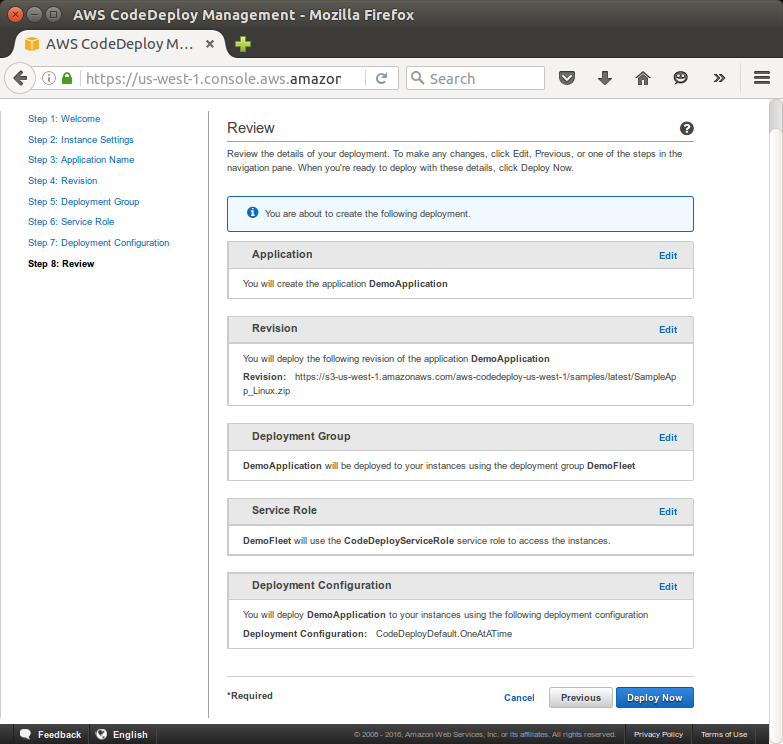
Click "Deploy Now":
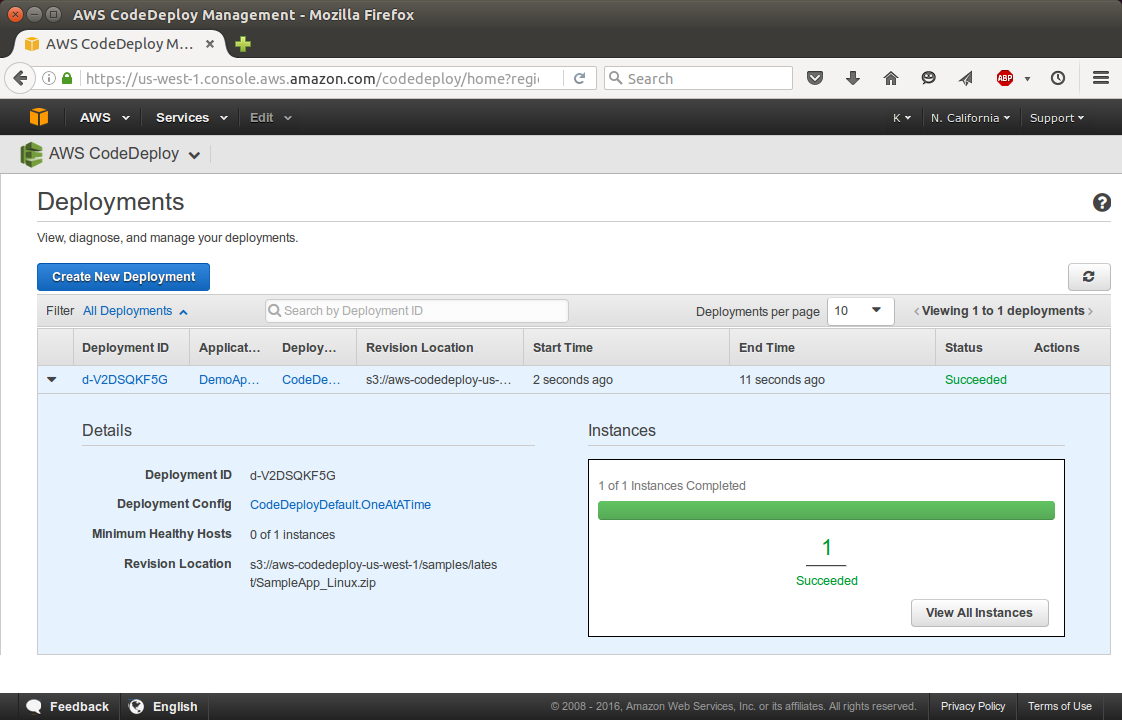
We will use the AWS CodeDeploy console to verify the success of the deployment.
We will use our web browser to view the web page that was deployed to the Amazon EC2 instance running RHEL instance.
In the list of deployments, look for the row with an Application value of CodeDeployGitHubDemo-App and a Deployment group value of CodeDeployGitHubDemo-DepGrp.
Since "Succeeded" appears in the Status column, we can now verify the deployment through our web browser. Our sample revision deploys a single web page to the instance.
Go to http://PublicDNS for the instance (for example, http://ec2-01-234-567-890.compute-1.amazonaws.com):

AWS (Amazon Web Services)
- AWS : EKS (Elastic Container Service for Kubernetes)
- AWS : Creating a snapshot (cloning an image)
- AWS : Attaching Amazon EBS volume to an instance
- AWS : Adding swap space to an attached volume via mkswap and swapon
- AWS : Creating an EC2 instance and attaching Amazon EBS volume to the instance using Python boto module with User data
- AWS : Creating an instance to a new region by copying an AMI
- AWS : S3 (Simple Storage Service) 1
- AWS : S3 (Simple Storage Service) 2 - Creating and Deleting a Bucket
- AWS : S3 (Simple Storage Service) 3 - Bucket Versioning
- AWS : S3 (Simple Storage Service) 4 - Uploading a large file
- AWS : S3 (Simple Storage Service) 5 - Uploading folders/files recursively
- AWS : S3 (Simple Storage Service) 6 - Bucket Policy for File/Folder View/Download
- AWS : S3 (Simple Storage Service) 7 - How to Copy or Move Objects from one region to another
- AWS : S3 (Simple Storage Service) 8 - Archiving S3 Data to Glacier
- AWS : Creating a CloudFront distribution with an Amazon S3 origin
- AWS : Creating VPC with CloudFormation
- AWS : WAF (Web Application Firewall) with preconfigured CloudFormation template and Web ACL for CloudFront distribution
- AWS : CloudWatch & Logs with Lambda Function / S3
- AWS : Lambda Serverless Computing with EC2, CloudWatch Alarm, SNS
- AWS : Lambda and SNS - cross account
- AWS : CLI (Command Line Interface)
- AWS : CLI (ECS with ALB & autoscaling)
- AWS : ECS with cloudformation and json task definition
- AWS Application Load Balancer (ALB) and ECS with Flask app
- AWS : Load Balancing with HAProxy (High Availability Proxy)
- AWS : VirtualBox on EC2
- AWS : NTP setup on EC2
- AWS: jq with AWS
- AWS & OpenSSL : Creating / Installing a Server SSL Certificate
- AWS : OpenVPN Access Server 2 Install
- AWS : VPC (Virtual Private Cloud) 1 - netmask, subnets, default gateway, and CIDR
- AWS : VPC (Virtual Private Cloud) 2 - VPC Wizard
- AWS : VPC (Virtual Private Cloud) 3 - VPC Wizard with NAT
- DevOps / Sys Admin Q & A (VI) - AWS VPC setup (public/private subnets with NAT)
- AWS - OpenVPN Protocols : PPTP, L2TP/IPsec, and OpenVPN
- AWS : Autoscaling group (ASG)
- AWS : Setting up Autoscaling Alarms and Notifications via CLI and Cloudformation
- AWS : Adding a SSH User Account on Linux Instance
- AWS : Windows Servers - Remote Desktop Connections using RDP
- AWS : Scheduled stopping and starting an instance - python & cron
- AWS : Detecting stopped instance and sending an alert email using Mandrill smtp
- AWS : Elastic Beanstalk with NodeJS
- AWS : Elastic Beanstalk Inplace/Rolling Blue/Green Deploy
- AWS : Identity and Access Management (IAM) Roles for Amazon EC2
- AWS : Identity and Access Management (IAM) Policies, sts AssumeRole, and delegate access across AWS accounts
- AWS : Identity and Access Management (IAM) sts assume role via aws cli2
- AWS : Creating IAM Roles and associating them with EC2 Instances in CloudFormation
- AWS Identity and Access Management (IAM) Roles, SSO(Single Sign On), SAML(Security Assertion Markup Language), IdP(identity provider), STS(Security Token Service), and ADFS(Active Directory Federation Services)
- AWS : Amazon Route 53
- AWS : Amazon Route 53 - DNS (Domain Name Server) setup
- AWS : Amazon Route 53 - subdomain setup and virtual host on Nginx
- AWS Amazon Route 53 : Private Hosted Zone
- AWS : SNS (Simple Notification Service) example with ELB and CloudWatch
- AWS : Lambda with AWS CloudTrail
- AWS : SQS (Simple Queue Service) with NodeJS and AWS SDK
- AWS : Redshift data warehouse
- AWS : CloudFormation
- AWS : CloudFormation Bootstrap UserData/Metadata
- AWS : CloudFormation - Creating an ASG with rolling update
- AWS : Cloudformation Cross-stack reference
- AWS : OpsWorks
- AWS : Network Load Balancer (NLB) with Autoscaling group (ASG)
- AWS CodeDeploy : Deploy an Application from GitHub
- AWS EC2 Container Service (ECS)
- AWS EC2 Container Service (ECS) II
- AWS Hello World Lambda Function
- AWS Lambda Function Q & A
- AWS Node.js Lambda Function & API Gateway
- AWS API Gateway endpoint invoking Lambda function
- AWS API Gateway invoking Lambda function with Terraform
- AWS API Gateway invoking Lambda function with Terraform - Lambda Container
- Amazon Kinesis Streams
- AWS: Kinesis Data Firehose with Lambda and ElasticSearch
- Amazon DynamoDB
- Amazon DynamoDB with Lambda and CloudWatch
- Loading DynamoDB stream to AWS Elasticsearch service with Lambda
- Amazon ML (Machine Learning)
- Simple Systems Manager (SSM)
- AWS : RDS Connecting to a DB Instance Running the SQL Server Database Engine
- AWS : RDS Importing and Exporting SQL Server Data
- AWS : RDS PostgreSQL & pgAdmin III
- AWS : RDS PostgreSQL 2 - Creating/Deleting a Table
- AWS : MySQL Replication : Master-slave
- AWS : MySQL backup & restore
- AWS RDS : Cross-Region Read Replicas for MySQL and Snapshots for PostgreSQL
- AWS : Restoring Postgres on EC2 instance from S3 backup
- AWS : Q & A
- AWS : Security
- AWS : Security groups vs. network ACLs
- AWS : Scaling-Up
- AWS : Networking
- AWS : Single Sign-on (SSO) with Okta
- AWS : JIT (Just-in-Time) with Okta
Ph.D. / Golden Gate Ave, San Francisco / Seoul National Univ / Carnegie Mellon / UC Berkeley / DevOps / Deep Learning / Visualization